When people find out that I have a passion for Microsoft 365 and all things cloud-based, one of the first things I hear from them is,
“Why do we get so many phishing e-mails at my work?”
“We got ‘hacked’ even though we are in the cloud, why?”
My answer to those questions is relatively simple;
Your I.T. team did not configure the available security setting to keep your organization safe.
Which is immediately followed by statements like
“So the cloud isn’t secure?”
“Why aren’t the security setting turned on?”
Those reactions are very valid but very naïve.
The world of smartphones, apps, and data being at our fingertips has led most people to assume that they (and their data) are safe online. But, if you have been paying attention to the news of late, you know that is not the case. Most smartphone apps steal personal data, track activity, and then share the data with Artificial Intelligence (A.I.) engines. The A.I. engines analyze that data, and the companies that run those engines then sell the completed analysis to advertisers.
That is why advertisers on Facebook, Google, Amazon, and others seem to know precisely what ad to display for you relative to your conversation (creepy, right?). When you find out about this, your first reaction is to remove the app that collects that data or use your smartphone’s privacy settings to limit what data those apps can collect on you. This is called “shared responsibility,” and it is the model that most cloud services operate on.
The shared responsibility model says that the cloud provider will make sure you have all the tools you need to secure your organization, employees, and data.
The shared responsibility model says that the cloud provider will make sure you have all the tools you need to secure your organization, employees, and data. Still, it is up to you to utilize and configure these tools. The last part of that sentence is what is key to why most companies continue to receive phishing e-mails, have data leakage, and have people with access to restricted data that they shouldn’t have. They assumed they were safe because they were in the cloud and did not configure any of the tools and settings to keep an organization safe.
There are many types of cloud services these days, including:
- Infrastructure as a Service (IaaS) – think Microsoft Azure, Amazon Web Services, Google Compute Engine, etc.
- Platform as a Service (PaaS) – think Azure SQL, Dynamics 365, Salesforce, etc.
- Software as a Service (SaaS) – think Microsoft Office / 365, G-Suite, etc.
And each of these offerings has some level of shared responsibility. The following table should give you an idea of what the cloud provider will secure and what the consumer is expected to secure:
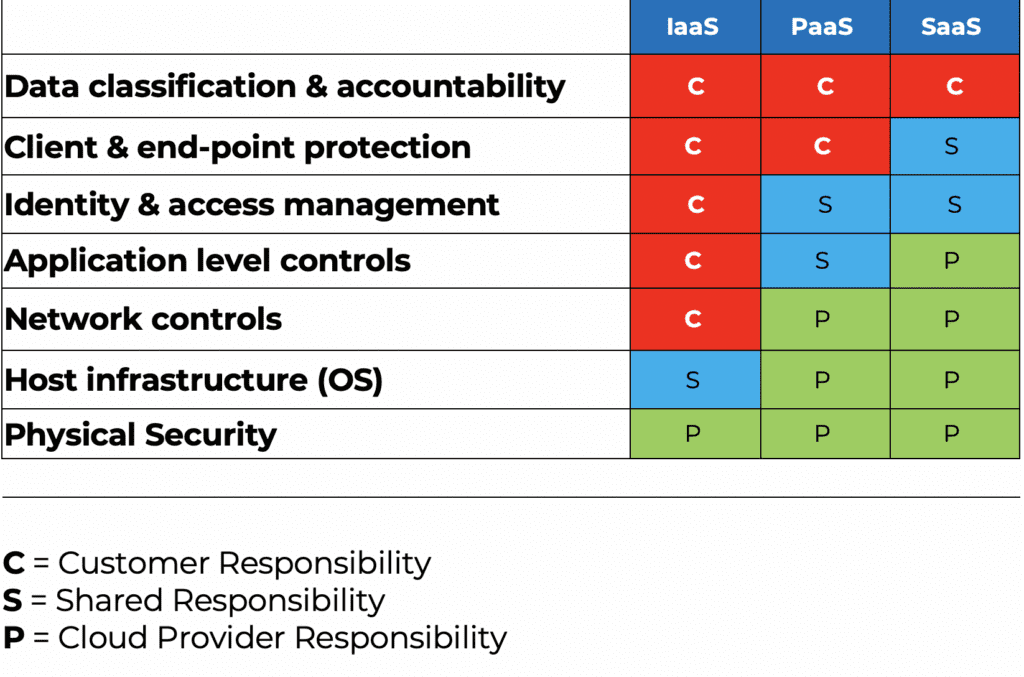
As you can see, it is up to the customer to secure, classify, and protect their data and clients. This part rarely gets done. Sometimes it does not get done because it is too overwhelming for an I.T. administrator to tackle. Sometimes it doesn’t get done because the I.T. administrator doesn’t know they need to do it. And sometimes it doesn’t get done because there is no one at the company knowledgeable enough to do it. Let’s take a look at all three of these scenarios:
It’s Too Overwhelming!

This, honestly, is the most problematic scenario for me. In these cases, the I.T. staff knows it needs to secure the service but doesn’t do it because of the amount of effort, coordination, and involvement required to complete it, or the company will not allow the investment in time and resources to get it done. Securing a cloud service takes a lot of effort and coordination between departments to ensure it is configured to meet any corporate policy and procedural requirements. Some examples include:
- Meeting data governance policies (i.e., who should have access to what, where should it be stored, and how long should it be kept).
- Meeting risk and compliance policies (i.e., does the company have to meet federal or industry standards like HIPAA, GDPR, PCI, PII, ISO-27001, etc.)
- Meeting Security policies [i.e., password policies, requirements for Multi-Factor Authentication (MFA), access based on security posture and location, etc.)
Most importantly, to carry out those requirements in a way that causes the least amount of disruption to the end-user. While this scenario is the most concerning, it is also the easiest one to address. In almost all cases, investing a little time and effort will yield tremendous gains, allow end-users to work more efficiently, and keep the company from undue risk and exposure.
I Don’t Know What to Do!

This one is probably the most common scenario. The I.T. team was looking to replace an on-premises solution, and the business pushed them to the cloud because all their peers were doing it. The I.T. team doesn’t know anything about the overall cloud solution they are leveraging, so they don’t know how to configure it, secure it, or fully utilize it.
I will use a concrete example for this; e-mail. Many companies ran their e-mail system but found them too complicated, too expensive, and too insecure to continue running them locally. The business tells the I.T. team they don’t want that risk anymore and shift the workload into the cloud. The I.T. team migrates to a cloud-based e-mail solution but does not realize that they have to configure all the settings to keep their end-users safe from phishing e-mails with unsafe links, trojan horse attachments that look like invoices from vendors, etc. Also, the I.T. team did not realize that with the licensing for the cloud-based e-mail system, they also have access to a laundry list of other online services like cloud-based data storage, collaboration tools, remote management tools, and security tools that end-users find on their own and start to utilize.
I see this all the time with 365. People purchase it to replace Exchange and do not realize that Exchange Online is just a fraction of the online services they get access to when purchasing Microsoft / Office 365. In addition to Exchange online, they get other services like:
- SharePoint: A modern-day intranet and file storage replacing on-prem solutions.
- OneDrive: Save your files and photos to OneDrive and access them from any device, anywhere.
- Teams: More ways to be a team through collaboration, communication, and online meetings.
- Stream: Engage and inform with video-based lectures, presentations, and webinars
- Azure Active Directory: Authentication, identity management, and multi-factor authentication
- Security and Compliance Center Ensures companies follow security best practices by providing practical steps that include:
- An overall security score
- Steps to take to improve that security score
- Access to additional settings to help meet the company’s data governance, risk, compliance, and security policies across all the 365 services.
To compound this problem, the different licensing options in Microsoft/Office 365 adds to the confusion. At the moment, there are 13 primary 365 licenses:
- Microsoft 365 Small Business Basic
- Microsoft 365 Small Business Standard
- Microsoft 365 Small Business Premium
- Microsoft 365 Business Apps
- Office 365 F1
- Office 365 F3
- Office 365 E1
- Office 365 E3
- Office 365 E5
- Microsoft 365 F1
- Microsoft 365 F3
- Microsoft 365 E3
- Microsoft 365 E5
And in addition to those, there are over 13 additional add-on licenses to expand the 365 ecosystems’ capabilities. Not understanding the licenses can lead to gaps in security and compliance that are required for your organization.
Once I.T. Teams realize everything that can be done with their solution, the “I Don’t Know What to Do!” scenario often quickly shifts to the “It’s Too Overwhelming!” scenario! Not taking the time to understand the solution they have purchased, making sure they have purchased the right licenses and add-ons, and allowing end-users to discovery on their own everything they have access to leads to data sprawl, data leakage, and insecure access controls that can put a company at undue risk and exposure.
I’m Just an Office Manager, Not an I.T. Person!

This scenario is widespread in small to mid-size businesses. There is someone who works there that is somewhat tech-savvy, or they have a kid who is a gamer, or there is no one else to do it, so they get tasked with helping everyone else use the cloud to get their job done. This scenario is straightforward to address, and probably one of my favorite ones to address: The business needs to partner with a Managed Service Provider (MSP) to help them run their I.T. services. A good MSP comes in to understand your business, business goals, and business challenges and help you map out how you can best utilize your cloud services to meet those needs securely and efficiently.
In all three scenarios, engaging an MSP is always a good idea. They have I.T. Professionals trained to help keep your business safe, understand the complexities of cloud services, and (in many cases) are cheaper than adding a full-time equivalent (FTE) to get the job done.

Will Smothers is the Team Leader of Edafio Technology Partners Cloud Computing services. He is responsible for driving product strategy, engineering, and operations of Edafio’s cloud services. Smothers’ primary focus is on rapidly developing and growing its best enterprise-focused cloud platform and delivering the most secure, reliable, cost-effective, high-performance infrastructure for running mission-critical workloads. Smothers joined Edafio in 2017, where he has attracted an influx of top engineering talent to build Edafio’s innovative next-generation cloud infrastructure. Before joining Edafio, Smothers was a technical leader at enterprise-level corporations, including the United States Army, Europe, Acxiom Corporation, and Nabholz Construction Corporation. With over two decades of IT experience, Smothers has led engineering initiatives across various cloud computing technology areas, from network engineering and system architecture to IT strategic planning for enterprises and database services. Smothers holds a BS in journalism from the University of Central Arkansas.








