Cybersecurity Maturity Model Certification: The New DoD Standard for Security
Cybersecurity is not just a trending topic; it is also a national security concern. With an increase in state-sponsored attacks (where one nation hacks another) as well as hackers-for-hire and other bad actors, it has become increasingly important that all sectors of the economy become more resilient to cyber-attacks. This also means that industries vital to United States operations, such as power, water, chemical, and manufacturing, must be better protected as they are becoming targets for attack.
To protect these assets, the Department of Defense (DoD) is issuing a new cybersecurity standard called the Cybersecurity Maturity Model Certification or CMMC. CMMC is designed to guide companies that are contracted by the DoD to strengthen their cybersecurity and help protect national assets. These assets do not just include things you might typically think about, such as defense systems but also include information about government infrastructures such as data related to dams, the power grid, nuclear power plants, and other similar items.
Any company or organization that bids on DoD contracts are required to meet the CMMC standards. In this blog, we are going to answer some of the questions surrounding CMMC as well as what companies can do to prepare for assessment.
Question 1: What exactly is CMMC?
CMMC is a DoD standard. This means that it provides a set of rules that govern how an organization runs its cybersecurity program to meet requirements created to protect sensitive DoD information, mainly in the form of Controlled Unclassified Information (CUI) and Federal Contract Information (FCI).
Companies must meet these rules to bid on DoD contracts. The company must have a third-party accredited assessor evaluate their program against the standard. CMMC is based on the NIST 800-171 standard and DFARS regulations, so if your organization has dealt with those standards previously, CMMC will be similar.
Question 2: What are CUI and FCI?
Controlled Unclassified Information is data sensitive to the DoD operations but not critical enough to be formally classified using the traditional secret/top secret system. Generally, this means any information related to the intellectual property, supply chain, or infrastructure workings of the DoD. This includes such things is atomic energy data, power grid, water supply, and other critical infrastructure. It also provides engineering information related to structures built for the DoD.
Federal Contract Information (FCI) is information related to federal contracts that are not available for public release.
Question 3: What does CMMC want me to do?
CMMC is based around the model that is broken up into two parts: Practices and Process Maturity. Each of these parts is further broken down into five different levels.
Level 1 is based on standard cyber hygiene. These are basic cybersecurity requirements that most organizations are probably already using by default.
Level 2 provides intermediate security requirements that create a robust, well-maintained cybersecurity program within an organization.
Level 3 requires an active cybersecurity program that is continuously evaluated using risk assessment practices. Level 4 and 5 create a proactive plan that is actively looking for threats and heading them off before they attack. CMMC requires that organizations at least meet Level 1 by meeting both the practice and process maturity requirements.
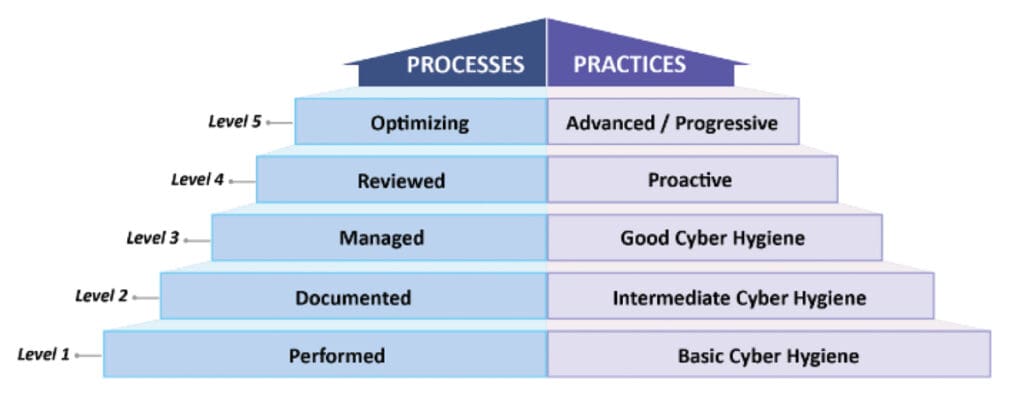
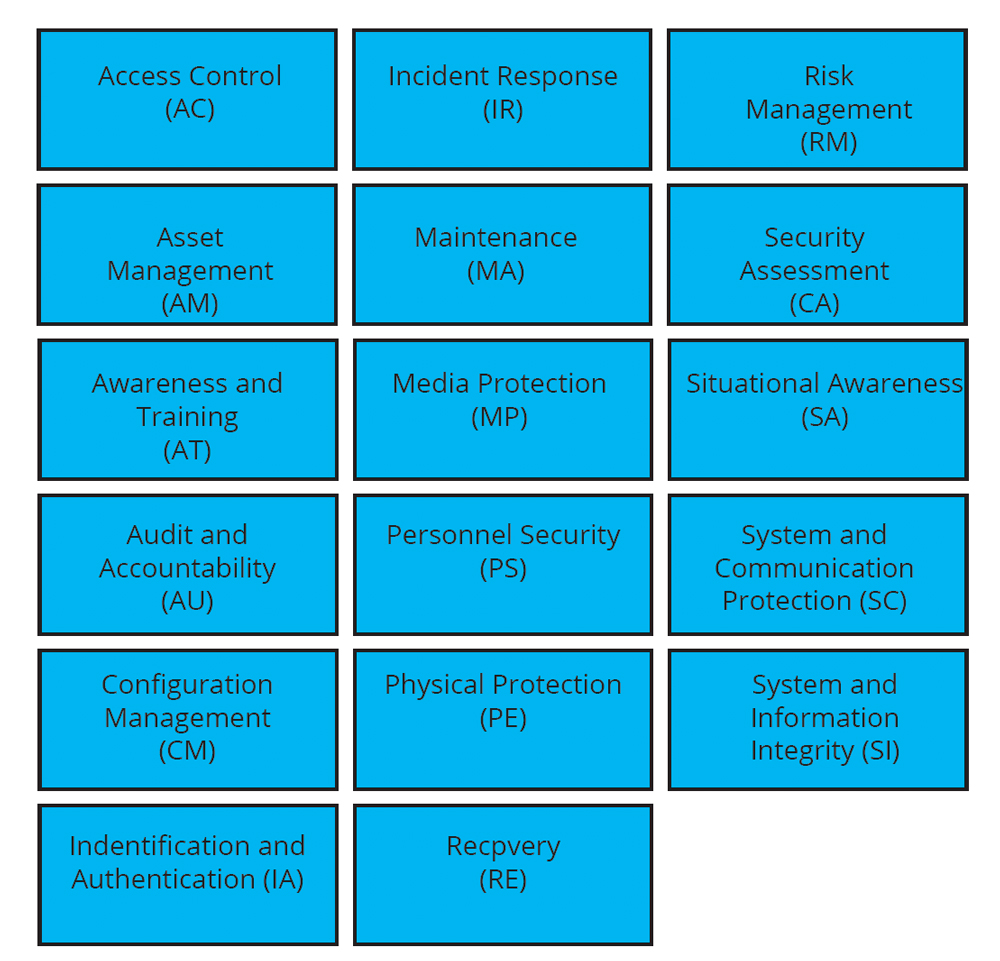
Practices are things that your organization has to do to meet the requirements of CMMC. These include things such as password complexity requirements, auditing security controls, using multifactor authentication, incident response, maintaining backups, security awareness training, and much more. Each level has a certain number of practices that must be met to be certified at that level. These practices are accumulative, meaning that all Level 2 practices must be met before you can be assessed at Level 3. Practices are broken down into 17 different domains.
Process Maturity deals with how you run your cybersecurity program. While there is no Level 1 requirement for Processes, Level 2 requires that every practice has an associated policy and procedure that documents how it is implemented and maintained inside an organization. Level 3 requires a risk management program that routinely assesses cybersecurity risk and ensures that the organization’s cybersecurity program is meeting that risk adequately.
Below is a breakdown of the requirements.
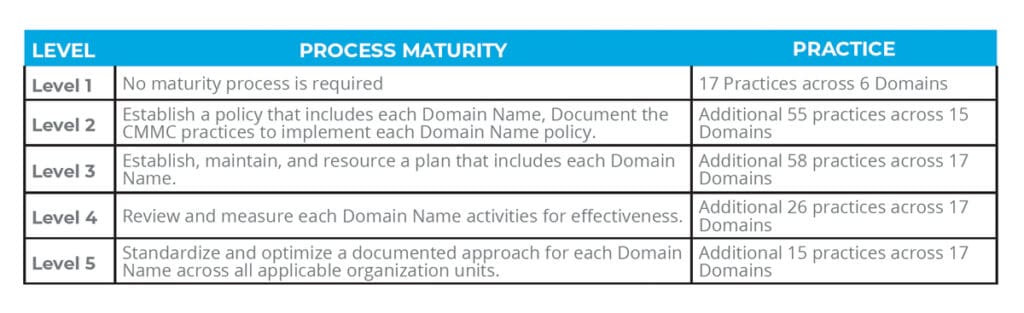
17 Practices across 6 Domains
Question 4: What level do I need to reach for my contracts?
While there has been no official requirement made, most indications seem to point to organizations having to meet Level 3 for all DoD requirements. Some specific, particularly sensitive contracts will require Level 4 and 5.
Question 5: Uh, that sounds like a lot, how long do I have to get this done?
CMMC cannot be done overnight. Even companies with excellent cybersecurity programs will likely have work to do to meet all the CMMC requirements. Fortunately, there is some time to get a start and work on this standard. DoD contracts will not require CMMC certification until November 2020, and there are currently no plans to add requirements to existing contracts.
Question 6: I’m a subcontractor to a primary, do I need to do this?
The short answer is yes. All contractors, whether they be sub or primary, must meet CMMC requirements. However, there has not been any official word on how subcontractors will be evaluated and what level they need to maintain.
Question 7: What’s this about third-party assessors?
CMMC cannot be self-certified. You must have a licensed, third-party assessor certify you at a specific CMMC level. Currently, the accreditation body for CMMC is working on training and licensing third-party organizations. Right now, no organization can certify you or claim to certify you.
Question 8: What can I do right now to get ready?
The best thing to do right now to get ready is to start working on implementing practices in CMMC. The first step is to do a gap analysis to see what you are missing from the desired CMMC Level. Once you understand what you need to do on the practice side of things, you can start to look at the process of maturity, which requires ongoing work and can not be done overnight.
Question 9: I’m feeling a bit overwhelmed now, is there any place I can get help?
Absolutely! For more information on CMMC, you can visit two places. The official CMMC website (https://www.acq.osd.mil/cmmc/) includes all the documentation of practices and processes as well as answers to questions. You can also visit the official accreditation body website (https://www.cmmcab.org/), which provides additional information about how CMMC will be implemented, including a plain language guide to each of the practices to help you better understand what you are looking for.
You can also reach out to a security consultant group like Edafio Technology Partners to help you implement the standard. Our Edafio security team can help you understand the tiers, create policies, procedures, and guide the implementation of CMMC to ensure you are ready in December when it comes time to assess.
Question 10: What if I have more questions about CMMC?
You can feel free to reach out to Edafio to answer any questions about CMMC as well as what you can do to prepare and how Edafio can help get you to the level you need. Fill out the form, and an Edafio consultant will be in touch with you shortly.
Download CMMC Info Sheet
If you’re interested in downloading a simple information sheet with everything you need to know about Cybersecurity Maturity Model Certification, fill out the form below:








