Cybersecurity Trends You Should Be Watching for 2021
With all the changes businesses faced in 2020, you’d think you might get a break when it comes to cybersecurity. But, cybersecurity trends show you still have to be diligent in 2021.
The days for just worrying about brute force attacks are long gone. Now, cyberattacks are far more sophisticated, making them harder to detect and prevent.
Of course, knowing what to look for, establishing a healthy cybersecurity plan and staying ahead of the trends help your business focus more on doing business than recovering from attacks.
1) BYOD Increases Variety Of Threats

Even before 2020 forced a dramatic shift to remote work, many businesses had BYOD (bring your own device) policies in place. In fact, 67% of employees use their personal devices at work, not just remote work. While 39% of companies have a formal BYOD policy, only half of the employees have received any usage and security instructions.
The increasing use of BYOD can benefit both employees and businesses. But it also makes cyberattackers happy. Without a plan in place to secure every device, including access to sensitive company information, your business is at risk in a variety of ways, such as:
- Devices being lost or stolen, leading to loss of data and a higher breach potential
- A device being hacked due to little to no security measures, opening the door to your business’s network
- Malicious apps on devices breaching networks
- Employees stealing company data, especially if anything’s stored on their device when they quit or get fired
You can’t rely on employees to think as much about cybersecurity as your business does. Having a BYOD cybersecurity plan in place is critical for managing devices and securing company data.
2) IoT Security Still Weak
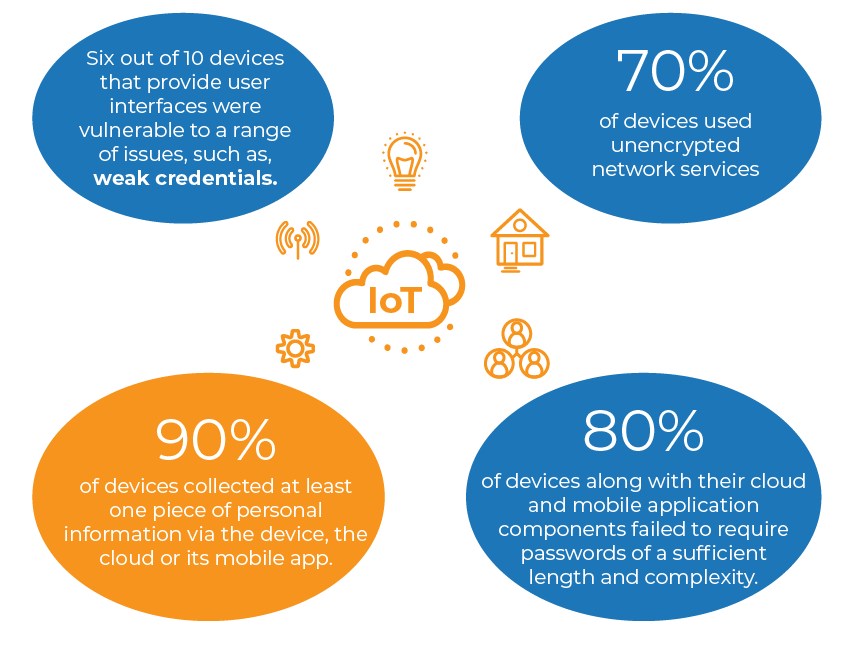
One of the most significant and most surprising cybersecurity trends in 2021 is IoT security is still weak. The IoT industry isn’t new, but security still isn’t a priority. This is a massive issue for both individuals and businesses.
Weak password authentication and little to no encryption are just the start of the security flaws plaguing IoT. Yet, your business likely uses quite a few of these devices. Even your employees probably use some at home, which can affect your company’s network if they’re also using their personal devices for work.
IBM points out several security challenges, such as managing updates, securing data storage and device-to-device communication. All of these are points of entry to your network if not carefully managed.
3) Cloud Services Are A Shiny New Target
The cloud is just so convenient that it’s seemingly impossible not to take advantage, right? Hackers think the same thing. That’s why they’re always looking for easy access, along with using the cloud to distribute their ill-gotten gains. For instance, Wyze got hacked due to a simple human error in removing security protections to the cloud-based database. Even Microsoft cloud customers were exposed in a more recent attack.
The cloud’s supposed to be secure, so what’s going wrong? Cloud usage is growing, but cloud providers only secure the basic infrastructure on their end. It’s up to individual companies to secure their own data beyond that. Naturally, it’s complex, to say the least, especially when managing access to various providers businesses use to store data and replace everyday services, down to their entire infrastructure is cloud-based.
The good news is security tools are becoming more sophisticated as well to combat attacks. These tools make IT administration much more manageable, drastically reducing the chance of human error and other cybersecurity issues.
4) Embracing Zero Trust Models
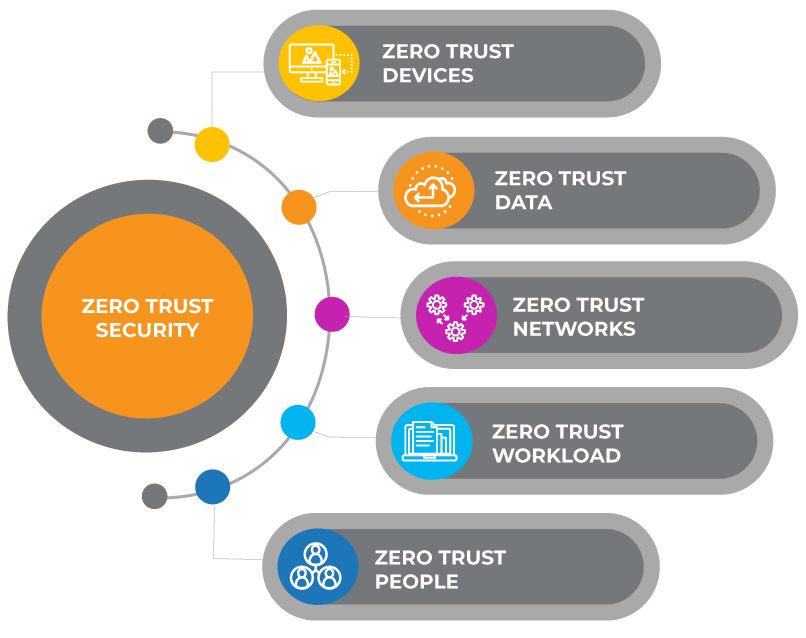
Businesses are starting to embrace zero trust models as an added layer of security. In terms of cybersecurity trends, this is actually a good thing. Zero trust models limit what comes in by not trusting new connections by default. Think of it as another wall that hackers have to get through, except this one doesn’t give way easily, making hackers give up faster.
That’s also why it’s highly recommended to implement multi-factor authentication. A hacker might have a stolen password, but they usually don’t have a quick way to bypass MFA questions or requirements.
Instead of assuming that everything behind the firewall is safe, the Zero Trust model assumes each request is an attempted breach and requires verification before allowing the connection or opening a file. Whereas older models like castle and moat may have said Trust but Verify, a zero trust model says never trust, always verify.
Guiding Principles of Zero Trust, per Microsoft,
- Verify explicitly – Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
- Use least privileged access – Limit user access with just-in-time and just-enough-access (JIT/JEA), risk-based adaptive policies, and data protection to secure both data and productivity.
- Assume breach – Minimize blast radius for breaches and prevent lateral movement by segmenting access by the network, user, devices, and app awareness. Verify all sessions are encrypted end to end. Use analytics to get visibility, drive threat detection, and improve defenses.
While zero trust models can’t be fully implemented overnight, they’re an ideal way of locking down your network. This is especially helpful with the rise in remote workers.
5) Logging and Monitoring
The principle of keeping records on network and system activity has been around for decades; recent Supply Chain Attacks show just how critical it is to have comprehensive logging that can be used for discovery and detection.
Without log data to research and correlate, it can be nearly impossible to determine the impact and scale of an attack. Attacks happen; organizations must be monitored to detect and be able to “play the security camera footage” to see what transpired.
6) AI Bypassing Security Protocols
One of the more disturbing cybersecurity trends to watch for in 2021 is how hackers are using AI. Much like you might use AI to automate tasks, hackers use the same technology to learn and bypass security protocols. Since their programs are continually learning, they’re becoming more advanced with every successful attack.
From much more sophisticated phishing scams to an increase in overall attacks thanks to automation, hackers are turning AI against businesses.
7) Ransomware Holding Strong

This one shouldn’t come as a surprise. Ransomware is one of those cybersecurity trends we’ll likely keep seeing grow for years. Microsoft stated they had blocked 13 billion suspicious and malicious emails in just a year.
The healthcare industry has seen first hand how ransomware is growing. In general, cyberattacks rose 45% during the last few months of 2020: the most prevalent threat – ransomware.
With far more sophisticated attacks, ransomware is harder to spot and block. With so many different devices, including personal devices, in use, it becomes even more challenging to prevent. That’s why a comprehensive cybersecurity strategy is more important than ever going into 2021.
8) Supporting Remote Workers

While many businesses had already embraced remote work, at least partially, numerous companies had to suddenly shift to a completely remote work model during much of 2020. In fact, many are still doing it or at least providing employees the option to work remotely.
The truth is, most businesses weren’t prepared for the security nightmare that comes with this. You’re not only securing your own network but trying to connect devices, so they’re protected even on less than secure home networks. Plus, employees are using personal devices, which might not have your preferred security software installed.
Throughout 2021, businesses are still having to harden security to support remote workers. It’s not easy, but managing your remote workforce, or even hybrid workforce, becomes much easier with the right partner. Discover how Edafio’s cybersecurity services aid you in facing all these cybersecurity trends and more.
FInd us on Feedspot








