A CHECKLIST OF 10 CYBERSECURITY BEST PRACTICES
Cybersecurity is a topic of strategic priority to businesses of all sizes and sophistication. From the invoice fraud that saw Google and Facebook lose $61.3 million in unauthorized payments to the supply chain attack of 2021, cyber threats are proving to be a nuisance.
Cybersecurity is no longer an option going by the rising uptake of mobile solutions. Businesses of all sizes and sectors utilize mobile systems, networks, and technologies to power their operations. Thus, with the increased uptake of digital technology, and a reliance on new digital technologies, cybersecurity is becoming of strategic importance. Today, like never before, businesses are just one click away from data breaches. A slight breach is likely to cost millions in losses, alongside causing devastating implications like the loss of consumer identifying information.
So, what should your cybersecurity infrastructure look like? What particular features should define your cybersecurity posture and agility? In this article, we explore ten cybersecurity best practices your business should be using… now.
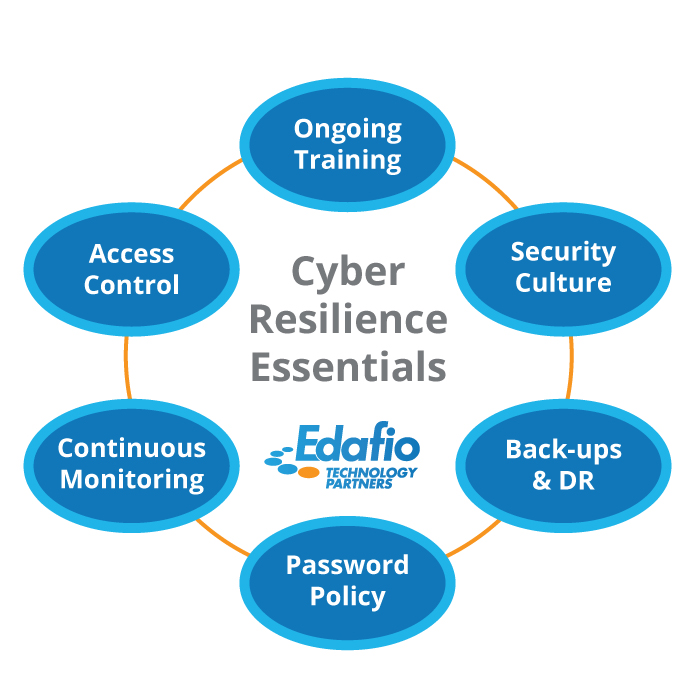
1. Cybersecurity Culture
Your employees are not going to care about cybersecurity because they are told to. They need an intrinsic inclination to protect your systems, endpoints, and networks. So, security needs to be perceived as a state of mind that is ever-present. It needs to transcend from something that is just said to something your employees genuinely want to do.
The best way to achieve cybersecurity is to weave a security culture into the company’s cultural fabric. Make it a behavior and a mindset to protect your computers, patch your networks and deploy administrative systems. Remember that adopting security tendencies from the bottom up helps integrate this culture and philosophy from the start.
2. Updating Applications and Operating Systems
Cybercriminals target glaring vulnerabilities in your networks and systems. Cybercriminals take advantage of unpatched networks, track, and spy on confidential data. Once they have access to shared networks and systems, they can wreak havoc by installing keyloggers that steal confidential information anytime you type.
Worse still, cybercriminals, like the attacks from Nation-States in China, Russia and North Korea can install ransomware that locks you out of your system and files, and demand payment to let you back. The software developers help fix the issues listed above by identifying and patching vulnerabilities. It is the responsibility of your virtual chief information officer or certified information security officer to ensure that your systems and shared networks are sealed from potential vulnerabilities. Most vulnerability fixes are contained in software updates. The sooner you install a security update, the least likely your business is at risk of cyberattacks.
3. Access Control
Cybersecurity administrative practices restrict unauthorized access to protected systems. Access control is a reliable security protocol to control who can access particular files, systems, or networks. The ultimate purpose of access control is to provide a level of security that mitigates the risk involved with unauthorized access. Without proper access and control, you can leave information critical to your organization open to your employees. This vulnerability yields problems such as data loss, breach or information theft, and violates data protection laws.
4. Maintain Current Back-Ups
The primary purpose of a data backup is to have a secure archive of your critical information, whether it is classified documents for your business or cherished photos so that you can restore your device seamlessly and quickly in the event of data loss. Think of a data backup as the foundation of your digital disaster recovery plan. By maintaining current backup of your devices, you are already one step ahead of any cyber threats that might result in data loss.
Use the 3,2,1 Backup Rule:
Create three copies of your data…on at least two storage solutions…and store one of them in a remote location.
1. Back up regularly.
2. Opt for more storage.
3. Don’t underestimate physical copies
5. Continuous Security Monitoring
The more sophisticated technology becomes, the more vulnerabilities it exposes. So, IT security personnel must confront and manage the security challenge negated by evolving digital systems. Implementing continuous security monitoring into the broader cybersecurity strategic plan is a logical technique to stay prepared. Constant security monitoring uses automated scanning to speed up remediation and to protect your data against external attacks.
6. Endpoint Detection and Response
Endpoints – the smartphones, laptops, tablets, and other devices we use regularly are a special target for cybercriminals. The easiest way someone can gain access to your files and personal information is by installing ransomware on your device. Voila! They have access to all your files, social media networks, and wherewithal.
Endpoint detection response EDR is one of the fastest-growing solutions to provide better security capabilities than traditional solutions. Unfortunately, companies are facing cyber threat challenges as criminals become highly proficient at maneuvering signature-based protections. In contrast, endpoint detection and response solutions are better than these signature-based legacy protections, as they aid with investigation and remediation efforts.
7. Be Aware of the Current Cybersecurity Threats
Information is knowledge, and knowledge is power. If you want to win, you need to know as much about your enemy as possible. Remaining safe and secure in the current digital age means educating yourself and learning about the emerging cybersecurity threats.
Right now, ransomware is the main offender that embeds your hardware and holds your data for ransom. Consider setting aside time to watch videos and read articles on what happened to others. Being aware of the latest cybersecurity trends helps you learn about what you need to protect yourself. You can use this knowledge to your advantage.
8. Mobile Device Encryption
With the rise in mobile devices, it makes sense that more companies are using their
devices to process, store, and transmit data. But with the increased use of technology comes the increase in security issues. One common problem is stolen or lost devices. Suppose your business deals with a lot of mobile devices that carry critical data. In that case, it’s a good idea to ensure none of that information falls into the wrong hands by implementing mobile device encryption.
One benefit of mobile device encryption is the sensitive information is protected. If a fully encrypted device falls into the wrong hands, the owner of the device can be sure that the data will not be used for unwanted purposes. Using mobile device encryption to secure your data correctly takes this extra step in security and protects yourself from liability.
9. Password Protect Wi-Fi Network
Mobile devices like tablets and mobile phones present a significant security challenge, especially given the flexibility of our everyday life. If your employees can access their emails and applications using cloud-sourced tools like OneDrive and Dropbox, they must have a passcode. The passcode secures any information or data should the device fall into the wrong hands. You can even configure the policies to erase data after a certain number of incorrect attempts. It’s a healthy security practice to protect your endpoints, even if it means adding a layer of security to access your mobile phone or tablet.
10. Have a Strong Password Policy
By educating employees on best password management practices is the company’s first line of defense against intruders. It is a constant endeavor to continuously improve and close security holes and ensure your users aren’t one of them. We recommend users to:
• Log out of systems they’re not using.
• Avoid writing down passwords
• Longer is Stronger: Take time and consider a strong/long password that they can remember.
• Multi-Factor Authentication
• Invest in a password manager
Final thoughts
Every day, a new business gets hit by a cyberattack. This includes government and education institutions, healthcare and companies of all sizes. Meaning anyone can become a victim of a cyberattack. The current trend suggests that such attacks will only increase in the future.
Security experts are already discussing what it means for SMBs to be cyber-resilient and how that can improve their overall cybersecurity posture. With cyberattacks increasing, being prepared ensures that businesses can withstand all threats and recover quickly in an actual attack or breach. Remember: embracing a proactive approach to cybersecurity makes businesses of all sizes more resilient.
Continuing to protect, detect, and respond moving forward, remember to follow the latest cybersecurity trends because hackers keep developing more sophisticated and creative ways to hurt your business.
With Edafio Technology Partners, you can respond to any cybersecurity incident and achieve better agility in your security posture.








